Data is the lifeblood of any organization. It is used to make decisions, drive innovation, and create competitive advantage. However, data is also a valuable asset to cybercriminals. As a result, it is essential for organizations to have strong data security measures in place.
There are a number of data security tools available, each with its own strengths and weaknesses. Here is a comparison of five of the most popular data security tools:
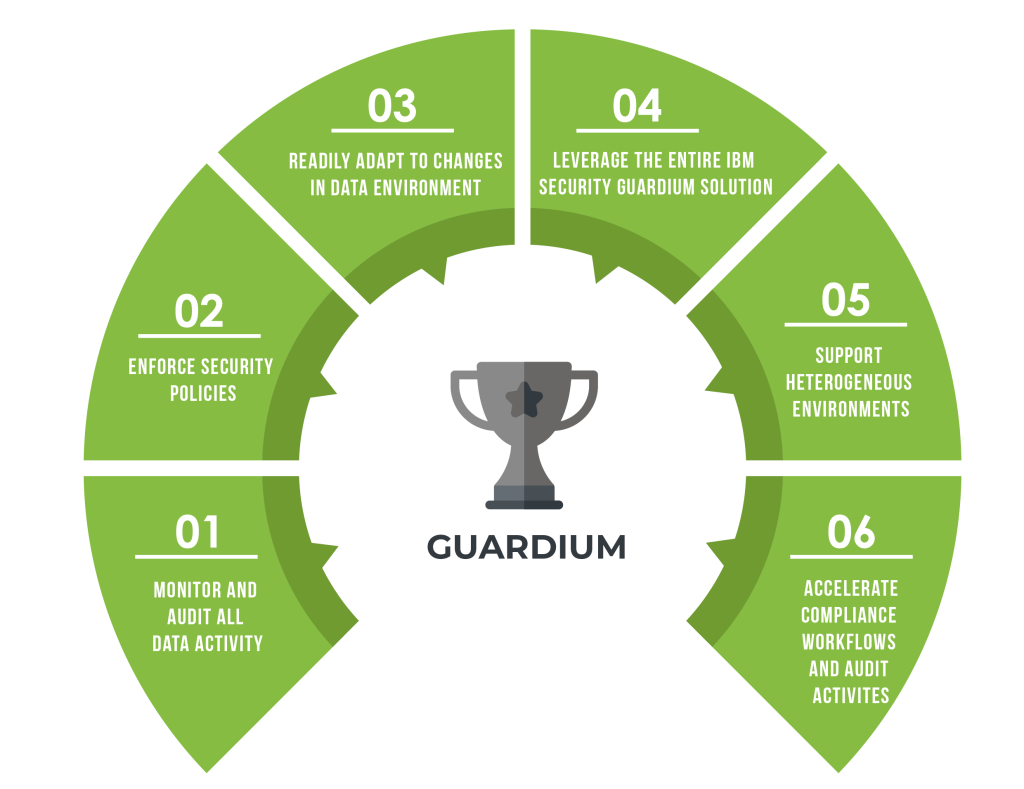
1. IBM Guardium: Defending Data with Vigilance
IBM Guardium stands as a stalwart defender of data integrity, offering a comprehensive data security and protection platform. Equipped with real-time monitoring, Guardium meticulously tracks database activities and user access. IBM Guardium is a comprehensive data security solution that protects data at rest, in motion, and in use. It offers a wide range of features, including data encryption, data masking, and data loss prevention.
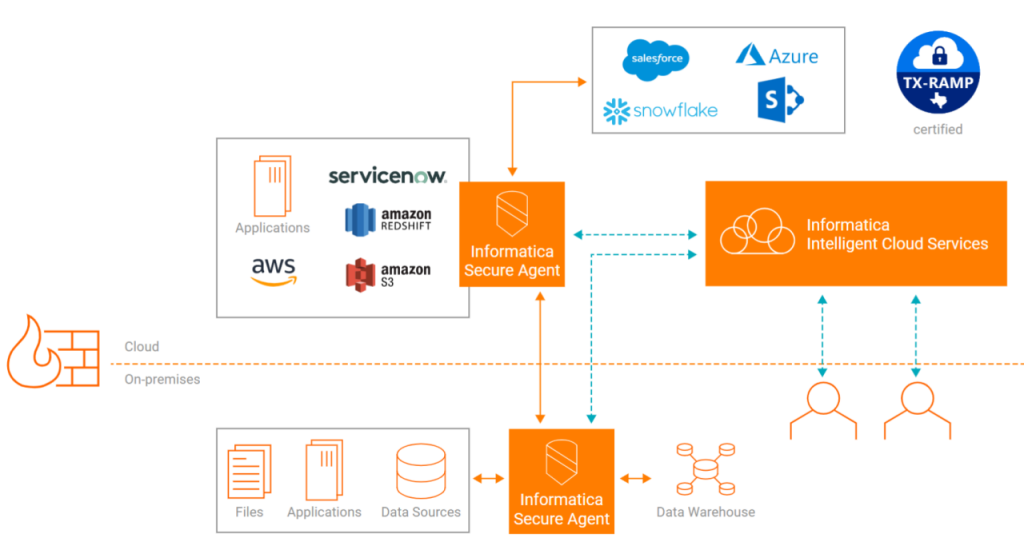
2. Informatica Secure@Source: Nurturing a Culture of Data Security
Informatica Secure@Source places emphasis on understanding the data lifecycle and fostering a culture of data security within organizations. Through metadata-driven insights, it helps identify and classify sensitive data, allowing administrators to monitor its movement and access. By mapping data flows across systems, Secure@Source establishes a comprehensive view of data movement patterns, enabling organizations to spot vulnerabilities and enforce appropriate access controls.
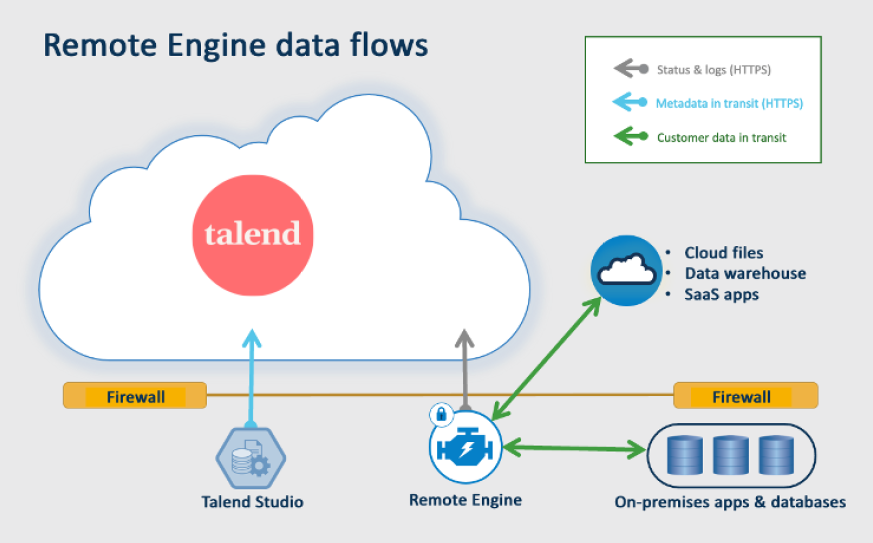
3. Talend Data Fabric: Weaving Data Security into Integration
Talend Data Fabric is an integrated data platform that includes a number of data security features. These features include data encryption, data masking, and data lineage. Its unified platform approach aids in consistent security enforcement across on-premises, cloud, and hybrid environments.
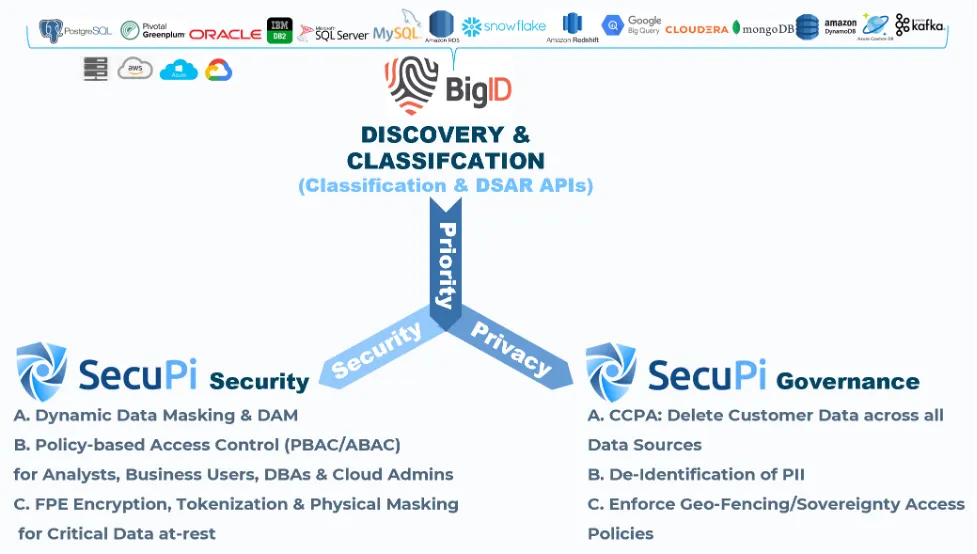
4. BigID: Discovering and Protecting Sensitive Data
BigID is a data intelligence platform that helps organizations discover, classify, and protect sensitive data. It offers features for data discovery, data classification, and data risk assessment. Using advanced machine learning techniques, BigID scans and identifies sensitive data, even in unstructured formats. Once identified, organizations can apply appropriate access controls, retention policies, and encryption mechanisms. BigID aids in minimizing the attack surface by pinpointing areas of high risk and fostering compliance with data protection regulations.
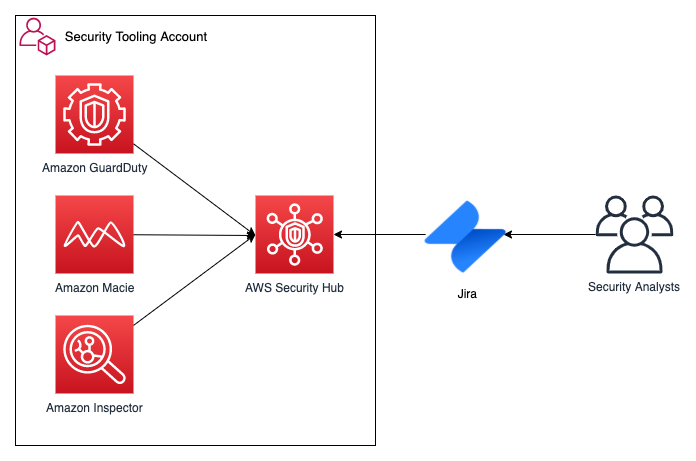
5. AWS Macie: Elevating Data Security in the Cloud
AWS Macie is a fully managed data security service that helps organizations discover, classify, and protect sensitive data in AWS. It offers features for data discovery, data classification, and data anomaly detection. Leveraging machine learning, Macie detects and classifies sensitive data stored within Amazon Web Services. It keeps a watchful eye on data access patterns and provides alerts for unusual behavior. Macie also aids in compliance with regulations like HIPAA, PCI DSS, and GDPR by offering automated data discovery and policy enforcement.
Conclusion: Building Resilient Data Fortresses
As organizations continue to grapple with the challenges of data security, these five tools emerge as champions of safeguarding digital assets. The evolving threat landscape necessitates a multi-layered approach to data protection, encompassing real-time monitoring, advanced classification, encryption, and compliance enforcement. Whether on-premises or in the cloud, data security tools play a pivotal role in fortifying the defenses of modern businesses. By embracing these tools and weaving them into their data strategies, organizations can build resilient data fortresses that stand strong against the tides of cyber threats.